Forward vs reverse proxy – Introduction
Forward vs reverse proxy – Proxy servers are frequently used when developing complex systems to enhance performance, security, and dependability. Between clients and servers, proxy servers help regulate traffic flow.
Forward proxies and reverse proxies are two proxy kinds that are frequently employed. While both are intended to increase a system’s performance and security, they operate differently and are employed in various situations. The distinctions between forward proxies and reverse proxies in system architecture will be discussed in this article.
What is Forward Proxy?
A forward proxy gives a client or a collection of clients proxy services. These clients occasionally share an internal network. One of these clients must first go through the forward proxy to connect to that file transfer server on the Internet.
A request may be approved or rejected depending on the parameters of the forward proxy. If the firewall approves, the request is routed to the file transfer server after that. The request was made by the proxy server, not the client, in the eyes of the file transfer server. As a result, the server addresses the proxy while responding.
Most commonly, a forwarding proxy is utilized for:
- Client Anonymity
- Caching
- Traffic Control
- Logging
- Request/Response Transformation
- Encryption
Forward proxy types
The many types of forward proxies are numerous. By their place of origin, the most popular ones are categorized. Residential proxies and data center proxies are the two types of proxies used in this situation.
- Residential proxies: An Internet Service Provider (ISP) with a physical address provides these proxies with actual IP addresses.
- Datacenter proxies: Because IP addresses originate from secondary sources like data centers, this form of proxy is not connected to an ISP.
What is Reverse Proxy?
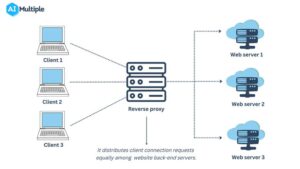
Redirects are different from reversals. Unlike the redirect name, the return name is made to the server name rather than the client (or request host). The reverse name receives requests from external clients on behalf of the servers behind it, as shown in the figure below.
A reverse proxy is a proxy that provides data transfer services to clients. The data transfer server runs behind the name that provides this service, which is unknown to the client. The return name hides the identity of the server, while the forward name hides the identity of the client.
Most commonly, a reverse proxy is utilized for:
- Server Anonymity
- Caching
- Load Balancing
- DDoS Protection
- Canary Experimentation
- URL/Content Rewriting
Reverse proxy types
All reverse proxies perform essentially the same functions. However, based on these qualities, we may distinguish between two major categories of reverse proxies. They are load balancers as well as standard reverse proxies.
- Regular reverse proxies: This name captures the requestor, sends it to the server for processing, and returns it to the client. The key to using this domain name is security.
- Load balancers: This domain is a subtype of the backend domain and connects to many backend instances. It manages client-server communication between all other servers and distributes traffic between them. This type of design is multipurpose, it changes the balance of multiple servers and improves speed and performance.
Top advantages of forward and reverse proxies
Reverse proxies
-
Load balancing
To prevent any one server from becoming overburdened, a reverse proxy evenly distributes incoming client traffic throughout the website’s back-end servers. One of the most well-known e-commerce websites is Amazon. Most likely, much incoming traffic comes in every second. With only one origin server, it is tough to manage all of this incoming traffic. Otherwise, it will be impossible to use the service due to overload. Reverse proxies assist website owners in distributing the heavy incoming traffic among several origin servers.
-
Caching
Clients can store frequently requested data on nearby servers for future requests with the use of reverse proxies. Clients can obtain the content more quickly thanks to caching. You are not required to always go to the same website when you need information. A reverse proxy, on the other hand, retrieves and saves data for you so you can reuse it with quicker access.
-
SSL encryption
Incoming client communication can be decrypted by a reverse proxy, and SSL/TLS can be used to encrypt and decrypt web server traffic. To ensure that no one can decipher the information transferred between servers and clients, all communications between web servers and clients are encrypted. This shields private information from unauthorized networks.
Forward proxies
-
An additional layer of security
Forward proxies serve as a security barrier between users and the internet to safeguard users’ systems from online threats. A proxy server keeps track of all network system incoming and outgoing traffic to look for suspicious activity and safeguard client data. While it functions like a firewall, the approaches and strategies they use differ significantly.
-
Webpage Crawl Rate
The amount of requests a web scraping bot may make to a website every minute, hour, or day is known as the crawl rate. Websites configure crawl rates to restrict web scraping operations. When you make repeated queries to the same website, it will identify your actions as suspicious and prevent access from your IP address.
Businesses can gather a lot of data using a proxy server while maintaining scrapers’ anonymity. For instance, to prevent website crawl rates, rotating proxies (a sort of forward proxy) regularly change clients’ IP addresses with each new request.
Leading Applications for Forward and Reverse Proxies
Forward proxies
-
Bypass Internet Censorship and Filtering
Your geographic position can be determined by websites that use IP-based geolocation, and access to Internet content can be restricted depending on users’ geolocation. To stop their residents from accessing illegitimate websites, for instance, governments censor some websites and their content. Censorship may also be carried out by private individuals or organizations for commercial or financial purposes. Businesses, for instance, may employ censorship to stop the dissemination of false information or rumors about their brands.
Users’ true IP addresses are concealed by a proxy server to shield them from being identified and followed while online. Additionally, it enables users to access geo-restricted websites and content from wherever.
-
Perform A/B testing for product pricing
Let’s say your business has just introduced a brand-new good or service. Based on the state of the market, you wish to improve your pricing approach. You must gather a sizable number of product price data from websites to find the best price for the good or service (price testing). Your data collection process can be sped up and enhanced with a web scraping bot. To stop web scraping, the majority of websites use IP bans and CAPTCHAs as anti-scraping measures. You can incorporate a proxy server into your scraper to get around problems with online scraping.
Reverse proxies
-
improve the website’s performance
To lessen the burden on internet servers and increase website responsiveness, reverse proxies can be used to cache website content. The reverse proxy caches and preserves web material, including images, videos, text, and other elements, when a user accesses a website for the first time. The reverse proxy will be positioned in front of the web server the following time a user accesses the same web page, forwarding the cached copy of the previously visited web page to the user. Website performance is enhanced as a result.
-
Prevent data breaches
For instance, Yahoo! was a victim of a data breach. 5001 million Yahoo user accounts, including names, email addresses, phone numbers, dates of birth, etc., were compromised in 2014. One of the finest strategies for organizations to use to safeguard their data from cybersecurity threats is encryption. By encrypting sent data via network traffic, reverse proxies assist organizations in preventing data breaches.
-
Restrict access to certain web content
Businesses may desire control over the information and websites that their employees have access to for sociological, ethical, or business reasons. Access to specific websites can be controlled using a reverse proxy server. Reverse proxies, for instance, can be used by corporations to block access to specific URLs that can be dangerous. The reverse proxy will deny any connection requests made by staff members to these specific domains.
Difference: Forward Proxy vs Reverse Proxy
The differences between the two proxy types are outlined in the table below:
| S.NO. | FORWARD PROXY
|
REVERSE PROXY
|
| 1. | The forward proxy connection starts inside the secured area and is intended for the outside of the insecure global network. | Reverse proxy connections originate from the public internet and are intended for private networks. |
| 2. | Application delivery does not use forward proxies. | The purpose of reverse proxies is application delivery. |
| 3. | Forward proxies work well for email security, dating, and content filtering. | Reverse proxies are used for application firewalls, content switching, authentication, and load balancing (TCP Multiplexing). |
| 4. | Internal users are prohibited from accessing user-filtered or otherwise restricted websites through forwarding proxy. | Reverse proxies prevent external users or clients from connecting directly to private or internal networks. |
Can a forward proxy also function as a reverse proxy?
Simply put, a forward proxy server cannot operate as a reverse proxy server. Even though the concepts behind these proxies may be similar, as we have discussed, they are used for quite diverse things.
An IP address is not all that a proxy is by itself. Proxies are made up of IP addresses and specific software that enables them to function as intended. Both forward and reverse proxies require distinct software to operate properly because they are used for various activities. Because of this, forward proxies cannot be used as reverse proxies.
Which of the two types of proxies is preferable for your company, forward or reverse?
Depending on your requirements and use cases, you should choose a forward or reverse proxy. Reverse proxies, for instance, may be helpful to manage all of the incoming traffic if your website receives a lot of daily traffic.
On the other hand, if you want to gather data from the stock market to examine price patterns and market trends, forward proxies are perfect for doing so without running the danger of being blocked.
Wrap Up
When browsing the internet, accessing geo-restricted content, web scraping, and other activities, forward proxies are essential for privacy and security. Reverse proxies are important for websites that get a lot of traffic every day because they prevent overloading and are good for SSL encryption and content caching.
Forward proxy and reverse proxy often work differently. They cannot be considered the same agent as they are used for different functions.