Uses of the TCP/IP Model
The uses of the TCP/IP model are considered while making use of your preferred websites or programs, it is smooth to disregard how the networks work. But a lot relies upon networks, computer systems, and websites quietly speaking to each other in the heritage. The inspiration of the net is the TCP/IP conversation protocol. Its four-level structure is a streamlined version of the OSI Model. You might be wondering why the TCP/IP paradigm, rather than the OSI model, is employed in the current Internet architecture.
The TCP/IP paradigm, which is extremely scalable and capable of determining the network’s most effective route as a routable protocol, provides the solution to this query. Because of this, it is frequently utilized in modern internet architecture.
To know the difference between OSI and TCP/IP model, read the article
Difference between OSI and TCP IP Models – Full Comparison
In this article, we shall cover layers of the TCP/IP model and uses of the TCP/IP model.
However, before delving deeply into the various facets of the TCP/IP model, we shall first examine the model’s definition and significance in detail.
What is the TCP/IP model?
Transmission Control Protocol/net Protocol (TCP/IP) are two specific communique protocols. TCP splits a message to packets which had been transmitted throughout the net whereas the IP is responsible to address every packet hence a threat ahead of the exact destination.
Previously, there has been no TCP/IP and no technique for the computers to perform effects over public networks. The principal feature of TCP/IP is that it governs how the statistics are sent and obtained in the form of packets between supply and destination.
So in brief, we are able to say that purpose of the TCP/IP model is to define communication in a community as a way to send information in the form of packets. IP manages how to make the path for packets to make certain it reaches their described destination. Before the records are dispatched their IP cope with is checked then it’s far decided in which to forward the facts.
TCP/IP uses the identical model as the Open Systems Interconnection (OSI) version. It makes use of the client/server model sort of conversation wherein a person or system (a customer) is furnished a carrier through another computer (a server) in the network.
Why TCP/IP model is important?
As it controls how computer systems send information from one device to any other, TCP/IP is vital. To make sure that the recipient gets the equal facts that were, to begin with, supplied, this information has to be saved specifically.
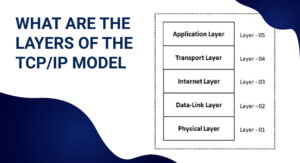
What are the layers of the TCP/IP Model?
The TCP/IP paradigm is composed of four separate layers, contrary to the OSI model’s seven layers. These layers are characteristic of a fixed of protocols while mixed. The TCP/IP paradigm distributes information via these tiers in a particular collection when a consumer is sending it, and then sends it again in a different collection as records are acquired.
Let’s now go through the specific roles played by each of these four layers in the protocol architecture.
- Network Access Layer
- Internet Layer
- Host-to-Host Layer
- Application Layer
Layer 1. Network Access Layer
The Network Access Layer is the bottom layer in the TCP/IP paradigm.
Computer systems can hook up with one another over the internet way to the community get the right of entry to layer, normally called the facts hyperlink layer. This includes network interface cards, cell modems, ethernet connections, pc tool drivers, and extra. Furthermore, it’s there where IP trades and virtual address mapping are accomplished. The software that transforms virtual information into highly communicable signals is an example of the technological infrastructure that supports access points and is included in the network access layer.
The IP packet is included within a “frame,” which is the Network Access layer Protocol Data Unit. Before sending a frame to the subsequent location on the physical network, a router replaces the previous payloads and trailers with new ones.
Other protocols at this tier include Fast Ethernet, Twisted Pair, and Fiber Distributed Data Interface (FDDI).
Network Access Layer’s Features
The following is a summary of some of the main tasks carried out by the network access layer in the TCP/IP model:
- The Network Access Layer defines how data is transmitted via a network.
- The data flow between two networked devices is mostly under its control.
- This layer is responsible for operations like translating IP addresses into physical addresses and enclosing IP datagrams in network frames.
Layer 2. Internet Layer
This layer, which exists between the Transport and Network Access Layers in the TCP/IP paradigm, is the second one.
To guarantee that records are transferred fast and properly, the net layer manages the waft and routing of traffic. This sediment additionally reassembles the information packet in its place. While there is a lot of resistance, the community layer can require a touch extra time to add a report, however, there may be less probable that the disruption will taint the file.
This layer employs three separate protocols. These consist of:
- IP: Among the most important protocols since it reveals a device’s IP address, it is employed to create network connections. This protocol is used to select the transmission method for the data. The two most used IP versions are IPv4 and IPv6.
- Address Resolution Protocol: The IP address can be converted into a physical address via ARP.
- Internet Control Message Protocol, or ICMP, allows notifications about datagram faults to be delivered back to the user. ICMP promptly notifies the user of any network issues. It cannot resolve the issue; it can only alert the user to the faults.
Functions of the Internet layer
The following is an outline of the Internet layer’s primary duties:
- Sending data packets to their intended networks is one of the Internet layer’s primary duties.
- The Internet layer is in charge of handling IP datagram routing, which includes forwarding, path determination, and logical addressing.
- Scheduling algorithms are used at this layer to assist routers in learning about the many networks they can join and in sending error messages.
Layer 3. Host to Host Layer
Similar to the transport layer in the OSI model, the third layer in the TCP/IP paradigm, is responsible for information distribution. It details how much information must be transported when, where, as well as the rate. The messages the transport layer gets from the application layer are put to use. The transport layer also offers a reliable informational link that links two network nodes.
In this layer, the following two primary protocols are present:
- TCP: The Transmission Control Protocol is a dependable communication procedure and is a further essential component. It controls the data flow, including the order and division of the data.
- UDP: User Data Gram is a protocol without connections, making it less reliable but less expensive.
Here you can learn the difference between TCP and UDP communications.
https://www.youtube.com/watch?v=uwoD5YsGACg
Functions of the Host-to-Host Layer
- The transport layer splits the information into packets, guarantees the destination validates the packets it has received and examines the packets it received from the sender for accuracy.
- The major goal of this layer is to transmit data without error.
- For the purpose of building a sequence, it divides and adds up the messages received from the session layer into sections.
Layer 4. Application Layer
This is the topmost layer in this mode. The application layer describes how client programs and protocols interact with one another. The applications communicate with the transport layer services with the goal of using the network.
Furthermore, it specifies the standards used by TCP/IP applications. That includes email, messaging services, and cloud storage services for the majority of us. This is what the individual consumer observes and communicates with when data is sent and received.
This layer employs numerous protocols, a few are mentioned below.
- The Hypertext Transfer Protocol is the primary method of communication between web servers and devices (HTTP).
- TELNET: On the Telnet system, files can be viewed and maintained using the TCP/IP protocol stack.
- FTP: File Transfer Protocol enables simple file transfer, as the name implies.
- NTP: Network Time Protocol allows us to specify a single set using our computer to acquire data, enabling synchronization between the user and the server.
Features of the Application Layer
Let’s now examine some further features of the Application layer:
- Access to global data about various services and objects from dispersed database sources is made possible by the application layer.
- This layer contributes to resource availability, communication synchronization, and partner identification.
- Users can establish connections to distant servers via the application layer.
- Using the user interface, node-to-node communication takes place in this area.
- Additionally, it provides a range of email services.
Uses of TCP/IP
The uses of the TCP/IP model are the following:
- It most frequently refers to the transformation of information’s shape from the concrete physical layer to the abstract application layer.
- TCP/IP specifies the essential communication protocols used at each layer as data passes through and can be used to deliver webpages, email, interactive file sharing, and network-based remote computers to a server host’s file system.
Applications of the TCP/IP Model
Discover helpful details about how to utilize TCP/IP services and applications. Some applications of the TCP/IP model are:
Scripting Protocols
It supplies the dynamic ways and disperses the dynamic methods for identifying the servers.
Joining the Internet
Application servers and/or web servers must be configured in order to connect the IBM operating system with a networking service provider. The utilization of internet setup data and information is mostly what attaches.
Internet domain names
In actuality, they are executing host names and associating IP addresses using a distributed data type.
Configuring Dynamic Hosting
The TCP/IP standard includes DHCP, which in embedded programming uses a central server to control internet protocol addresses
Private Virtual Networking
In actuality, it allows a steady advertisement to expand their private process over the current framework of a public processor. As an example, VPN providers manage networking traffics while offering fundamental security measures, i.e., data protection.
FTP protocol for small files
A Simple protocol known as the trivial file transfer protocol (TFTP) allows for basic file transfers without the need for user authentication.
Conclusion
The TCP/IP model is regarded as a standard for data transfer across the internet. It breaks up communication into data packets to prevent sending the entire message again in the event of a transmission error. The four levels of TCP/IP allow for the standardization of the process without the involvement of software and hardware vendors. In this article, we discussed the TCP/IP levels, their purposes, and the protocols that these layers use. So here are some of the major uses uses of the TCP/IP Model.
TCP’s role is to gather and reassemble data packets, and IP’s role is to send the data packets to the right place.
TCP and UDP are both examples of transport layer protocols. While UDP is a connectionless protocol, TCP is a connection-focused protocol. This indicates that whereas UDP doesn’t quite need any connection before communicating, TCP does.